Osquery is a powerful security tool that provides a table-like interface to endpoint information that can be queried using SQL. It is an operating system instrumentation, monitoring, and analytics” framework powered by SQL.
Unfortunately osquery doesn’t provide a great deal of support for audits on Windows operating system. However, given its open and extensible nature, that problem has been solved thru a variety. Osquery is a multi-platform software, can be installed on Linux, Windows, MacOS, and FreeBSD. Osquery allows us to explore the operating system profile, performance, security and many more metrics by using SQL-based queries. In this tutorial, I will show you how to install osquery on the Linux distributions Ubuntu 18.04 LTS and CentOS 7. Quickly deploy osquery and scale your fleet to 50,000+ devices on top of a stable core technology. Get started with Fleet Programmable access to every device. Keep track of servers and containers wherever they live: on your own hardware, in Amazon/Azure/Google clouds, or a little bit of each. Osquery, a tool initially developed by Facebook. Lets you query your local machine just like a database. This flexibility to extract information from your assets using SQL leads to several use.
Osquery exposes an entire operating system as a high-performance relational database, which allows you to write SQL queries to explore detailed operating system data. With Osquery, SQL tables represent abstract concepts such as running processes, loaded kernel modules, open network connections, browser plugins, hardware events, or file hashes. This granular data represents a wealth of information that can be leveraged for threat investigation, remediation, and prevention that is now available through Orbital and SQL searches.
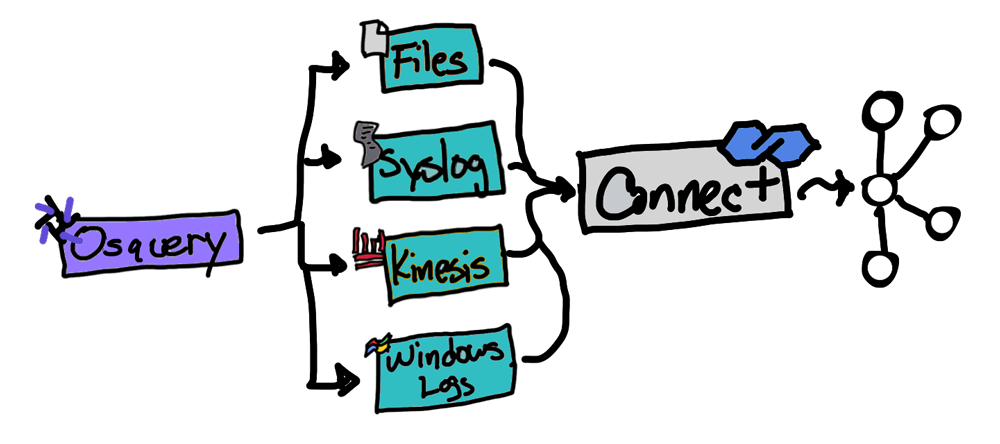
Cisco Orbital is a new service that allows customers to run queries against their endpoints using Osquery, which it uses as a query engine, extending it with additional tables. Applications such as AMP for Endpoints, Threat Grid, and Threat Response can ask Orbital to make detailed queries and send the results to other applications, such as a private data model for storage of query results as part of an investigation.

More Info
Osquery-java
- Query Basics - A high-level description of SQL queries, and how Orbital makes it possible to run complex queries against your endpoint data without the need to learn SQL first.
- Osquery.readthedocs.io - Osquery Documentationk
Osquery is an operating system instrumentation framework for Linux that exposes this operating system as a high-performance relational database so that SQL queries can explore the operating system data. With osquery, SQL tables represent abstract concepts such as running processes, loaded kernel modules, open network connections, browser plugins, hardware events, or file hashes.
AT&T Cybersecurity recommends that you install the AlienVault Agent on your Linux hosts to monitor endpoints and collect logs. Alternatively, you can use osquery to collect data and send them to USM Anywhere through syslog.
Note: Do not run osquery in parallel with the AlienVault Agent because it will interfere with the agent and cause USM Anywhere not to parse the data it receives.

You must have sudoA program for UNIX-like computer operating systems that allows users to run programs with the security privileges of another user, by default the superuser. privileges to complete the following procedure.
Osquery Windows
To collect logs from Linux using osquery
Osquery Windows Events
- If you do not yet have osquery, download it and follow the instructions appropriate for your operating system.
Create a text file called osquery.conf and copy-paste the contents of this file into it.
Important: After you copy-paste the text, make sure to edit it so that all strings with equals signs (=) in them remain on the same line. Otherwise, this procedure will fail.
- Save osquery.conf and copy it to /etc/osquery/.
Note: We recommend leaving the queries created by default, but you can create your own osquery configuration.
- Start the osquery daemon:
If you have not already done so, configure syslog to send data to the USM Anywhere Sensor. See Linux Log Collection with Syslog for instructions.
This should include restarting the syslog service.
Verify that you can see osquery events in USM Anywhere.
